The Terrorist Threat Cycle
Understanding the Steps to Enhance Personal and Community Safety
In this article, we’ll break down the Terrorist Threat Cycle (also known as the Criminal Threat Cycle) and how it applies to both security professionals and civilians alike, by focusing on:
♠️ Understanding the Cycle of Attack in order to anticipate and disrupt threats before they unfold
💀 Spot Vulnerabilities by recognizing what factors invite an attack and what to look for
♠️ Simplify the Steps by break down complex strategies for practical, everyday use
Let’s go!
Understanding the Terrorist Threat Cycle: A Blueprint for Awareness and Preparedness
In an increasingly complex world, understanding the behaviors and methodologies behind terrorist and criminal attacks has never been more crucial.
The Terrorist Threat Cycle provides a logical series of steps that follow the patterns of most terrorist and criminal activities.
While the consistency of these steps does not imply a direct connection between all attackers, it highlights a rational thought process among individuals capable of conducting risk/benefit analyses.
By familiarizing ourselves with this cycle, we can enhance our vigilance and improve personal and community safety.
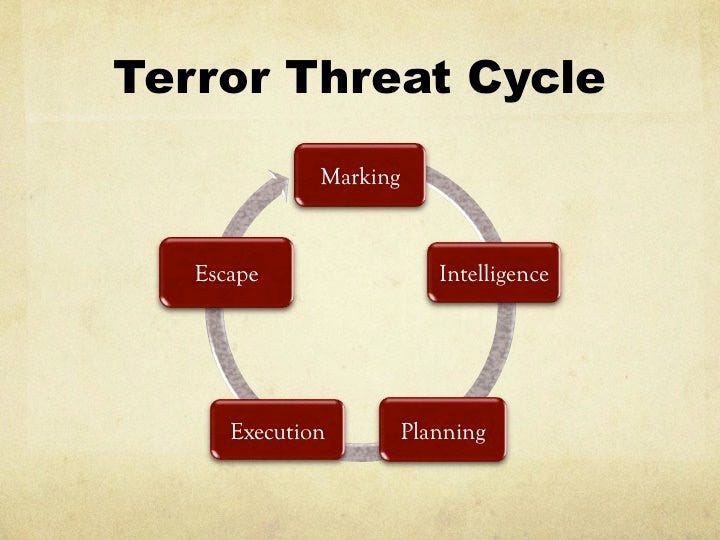
The Eight Steps of the Threat Cycle
The Terrorist Threat Cycle traditionally comprises eight steps. For clarity and practical application, we’ll simplify these into five primary stages, each encompassing the essence of the original steps:
Marking the Target: Identifying and selecting potential targets based on goals and objectives.
Intelligence Gathering: Collecting information about the target through surveillance and research.
Planning: Formulating a detailed attack plan, including logistics and resource allocation.
Execution: Carrying out the attack while continuing surveillance until the moment of action.
Escape: Planning for a getaway, which varies significantly based on the nature of the attack.
While these five steps simplify the original cycle, they encompass the core principles needed to understand the behavior of those who pose a threat.
Marking the Target
Marking the Target is the initial phase where potential targets are identified and narrowed down according to the attacker’s goals. Importantly, the target serves as a tool, not the ultimate goal.
For example, a terrorist might choose a crowded public area to maximize media attention and fear, while a criminal may select a vulnerable individual for personal gain.
Considerations for Marking the Target:
How “soft” is the target?
Access points and vulnerabilities
Existing security measures
Availability of information
Target Profile:
Terrorists: Focus on the publicity and psychological impact of their actions.
Criminals: Concentrate on financial or material payoffs.
When Timothy McVeigh was planning his bombing attack in the mid-1990s, he initially considered multiple sites in various states before settling on the Alfred P. Murrah Federal Building in Oklahoma City.
One key reason for this choice was the large parking lot in front of the building, which would provide ample space for news crews, cameras, and vehicles—offering the ideal vantage point to capture the destruction.
McVeigh's goal was not just to cause damage but to make a public statement through widespread media coverage.

Intelligence Gathering
Intelligence is the next critical phase, involving the collection of information about the target through various means, including personal observation (surveillance) and open-source intelligence. The duration of this phase can vary significantly.
For example terrorist cell planning a mass casualty event may involve weeks or months of meticulous planning, while a street mugging could take mere seconds as the attacker sizes up their victim.
The steps in the criminal or terrorist threat cycle are not linear, but rather interconnected, constantly influencing one another.
For instance, while an attacker may initially select a target, the intelligence gathered during surveillance could reveal new information that makes the original target too difficult or high-risk.
In this case, the attacker must reassess their goals, returning to the target selection phase to choose a more feasible option.
Planning
Once sufficient intelligence is gathered, the attacker shifts to Planning. This phase involves formulating an attack strategy based on the gathered information, resources, and capabilities. For sophisticated attacks, this may include:
Securing training and necessary equipment. This is also known as “tooling up.”
Conducting dry runs or rehearsals to refine their approach
Let’s illustrate this with the example of Nidal Hassan, the Ft. Hood shooter, who meticulously prepared for his attack. He purchased a FN 5.7 Herstal pistol, specifically requesting the "most high-tech pistol available."
To ensure proficiency, Hassan took handgun classes a month prior, secured a membership at a shooting range, and regularly practiced his marksmanship, further honing his skills in preparation for the attack.
His actions during this phase demonstrate the methodical nature of planning, as he built up the tools and capabilities needed to execute his violent intent.
Similar to the issues that may arise during the intelligence phase, complications may arise during the planning stage as well. For instance, logistical issues or resource limitations may come up, forcing the attacker to rework their approach or pivot to a different target altogether.
This fluid, adaptive process underscores the importance of understanding how each step in the cycle informs and modifies the others.
Execution
The Execution phase is where the gathered intelligence and planning culminate in action. Surveillance continues until the attack is initiated or aborted.
An attacker who has prepared adequately will spend less time in this phase, swiftly moving from plan to action.
For instance, in a robbery scenario, the longer an attacker surveils and prepares, the more likely they are to refine their execution for maximum effectiveness.
Escape
Finally, the Escape phase is crucial. It involves detailed planning to ensure a successful getaway. The sophistication of the escape plan often correlates with the complexity of the attack. A bank robber may require extensive planning for a safe exit, while a mugger might rely on speed and spontaneity.
Wrapping it up
By understanding the Terrorist Threat Cycle, security-minded individuals can better recognize potential threats and enhance their situational awareness. This knowledge not only aids personal safety but also contributes to community vigilance and preparedness.



